16k
Up to 16k new AiTM records per day
400%
We saw a 400% increase in AiTM activity between 2024 and 2025
23+
Additional feeds, allowing for further proactive blocking of malicious infrastructure
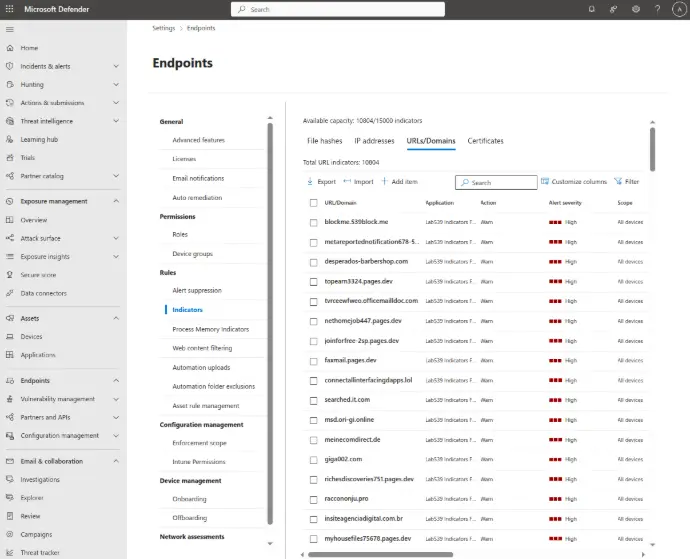
Seamless Microsoft Defender Integration
Simply enable this integration from within our portal and get indicators fed into your Microsoft Defender deployment in real time.
Block users from accessing AiTM infrastructure and raise alerts in your Defender dashboard when they do.
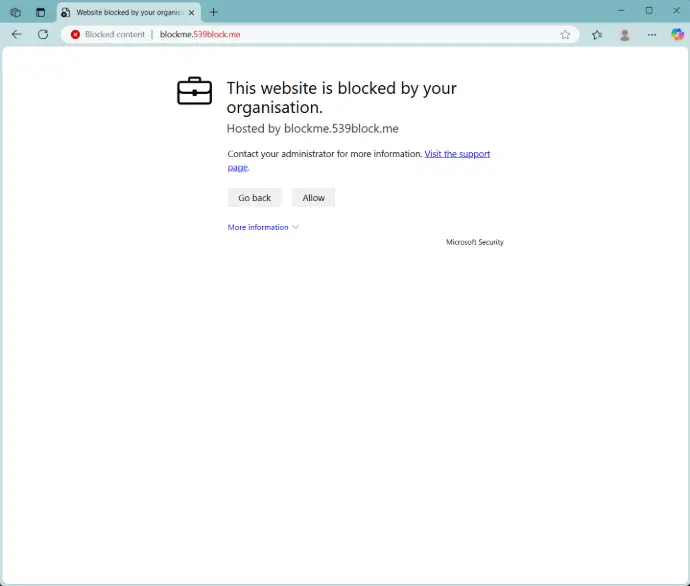
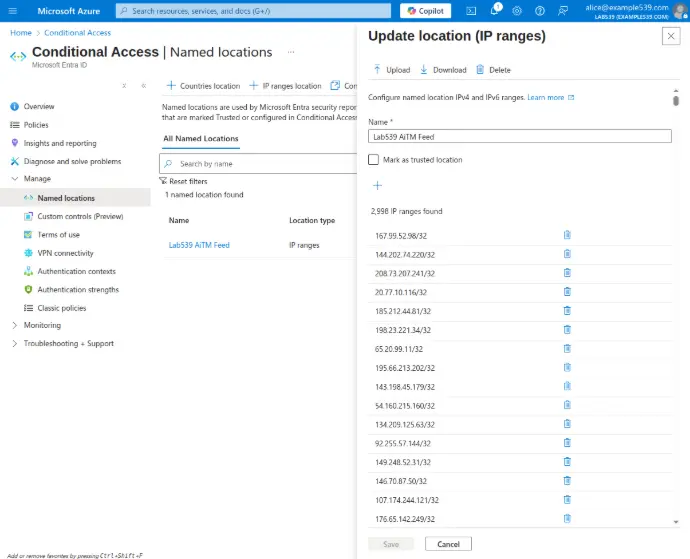
Conditional Access Policy Integration
Don't just prevent users from accessing AiTM infrastructure, but consume our named location feed in your conditional access policies in order to block authentication to your environment from AiTM infrastructure.
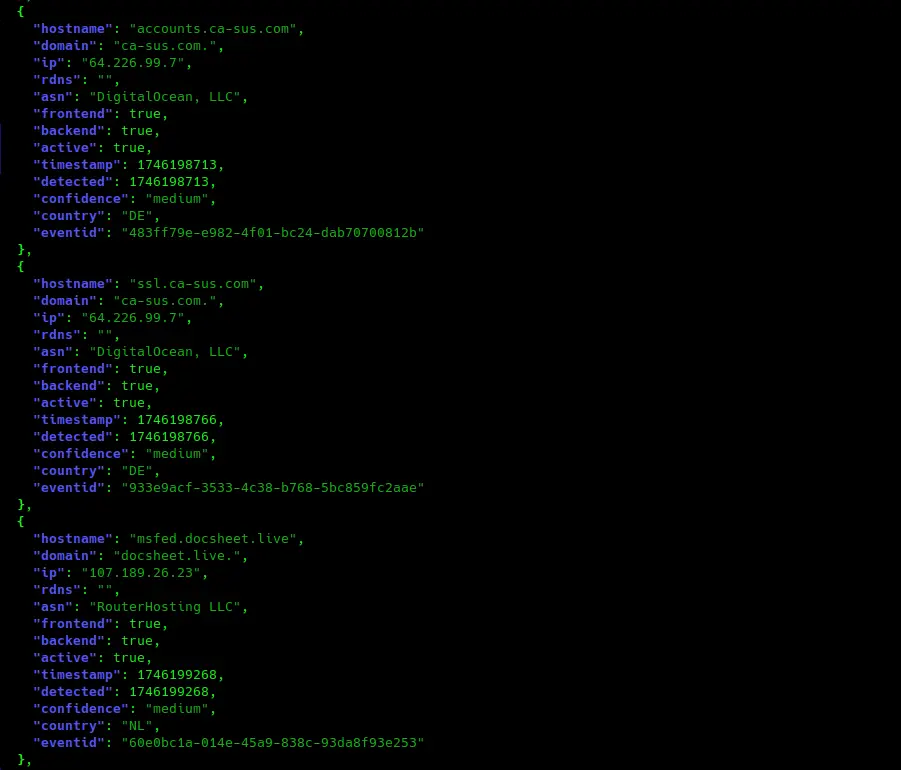
Full API access
We all have unique use cases, so we also make our data available in a flexible format via our API so that you can consume it however you wish.
We even let you pull down all recent data so you can run queries locally rather than via the API.
Great for custom use cases and great for investigations.
Why we are different:
We don't believe that there has to be victims for there to be threat intelligence. We don't dislike intel that comes off the back of breaches - Microsoft's identification of Void Blizzard in 2025 was a fantastic insight into some adversarial trade-craft... just a shame that multiple organisations had to suffer in order for those insights to be shared. That is the downside of reactive (or post event) threat intelligence, there typically has to be a victim.
Our focus, therefore, is proactive threat intel. We go out and hunt down adversaries, and in particular their infrastructure, so that we can let you know where it lives and enable you to block it. This approach is why we had the Void Blizzard infrastructure in our feed and actively blocked in the environments we operate in weeks before Microsoft customers even received phishing emails.
There is a huge difference between proactive and reactive intel. We know that most organisations will vastly increase their security posture, and reduce account takeover attacks by moving to a proactive approach. We know this because we see it first hand. It also means that when new tactics and techniques evolve we can already be across them. We're already blocking infrastructure used in ConsentFix campaigns (even before that technique had been publicly disclosed).
Reach out, or subscribe if you want to know more or give things a try.
Our latest content
Check out our latest adversary tracking blogs:


